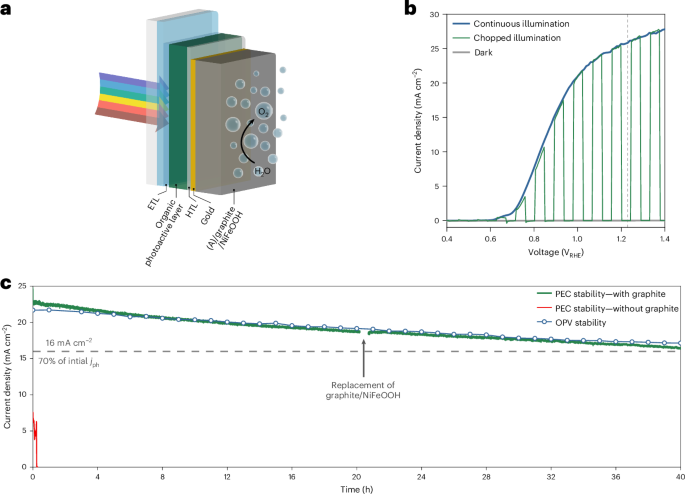
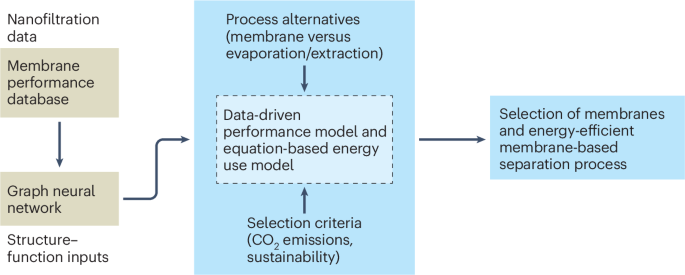
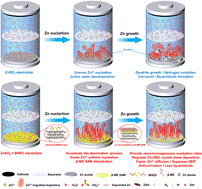
Pentagon’s use of commercial telecoms draw scrutiny after Chinese breaches
DOD inspector general plans three-pronged inquest at senators’ urging.

The inquest, which follows Chinese penetrations of U.S. telecommunications companies, will look at three ways the Pentagon uses unclassified commercial devices and services, Jaryd Bern, assistant inspector general for legislative affairs and communications, wrote in a March 20 letter to Sens. Ron Wyden, D-Ore., and Eric Schmitt, R-Mo.
Bern wrote that the IG would first look at the Pentagon’s Spiral 4 contract vehicle for buying mobile communications devices and services—specifically, its security requirements, how well they are enforced, and vulnerabilities in the SS7 telephony protocol. After that report is completed later this year, the office will turn to the encryption of unclassified data and voice communications in collaboration tools. Finally, the office will look into the “use of end-to-end encryption for unclassified voice communications using the desktop Plain Old Telephone System,” which has been replaced by VOIP services in many but not all DOD organizations.
Wyden welcomed the inquest in a Monday statement.
“The Department of Defense knew every major wireless carrier was vulnerable to foreign hacks before it agreed to spend billions with Verizon, AT&T and T-Mobile. It is disgraceful that DOD failed to even require the companies to adopt minimum cybersecurity defenses or turn over copies of their 3rd party audits,” he said. “The Inspector General deserves credit for also agreeing to investigate DOD's decision to buy dangerously insecure collaboration software, such as Microsoft Teams, which does not use end-to-end encryption by default, leaving DOD communications vulnerable to foreign hacks."
The Pentagon did not respond to a request for comment by press time.
Wyden and Schmitt had written to the DOD IG in December, urging an investigation after the China-backed Salt Typhoon effort penetrated up to 80 U.S. and foreign telecommunications providers. The breach reportedly allowed the hackers to access the communications of roughly 150 high-value targets, including people affiliated with then-President-elect Donald Trump.
Nextgov’s David DiMolfetta contributed to this report. ]]>