Army says DUCES to cyber hackers: New RFI looks for tactical edge zero trust solutions
“This constrained, highly dynamic, and adversarial-susceptible tactical environment will be a challenge to implement ZT solutions that meet mission needs,” the RFI stated.


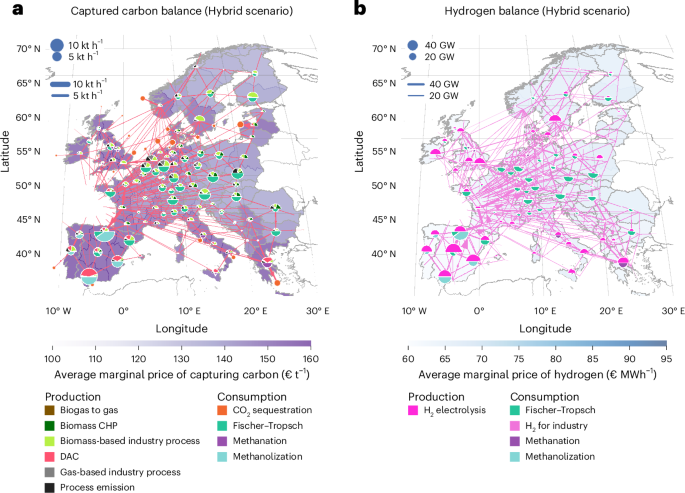
Sgt. Victor Sanchez, a fire direction coordinator assigned to Alpha Battery, 1st Battalion, 258th Artillery Regiment, 27th Infantry Brigade Combat Team of the New York Army National Guard, operates an advanced field artillery tactical data system. (U.S. Army National Guard photo by Sgt. Alexander Rector)
WASHINGTON — The Army is on the hunt for zero trust capabilities to ensure its data is secure in tactical network architectures, according to a request for information published Monday.
The service’s C5ISR Center is soliciting information from interested businesses to help find zero trust solutions that can “integrate seamlessly” into the Army’s existing infrastructure while operating in denied, degraded, intermittent or limited (DDIL) environments. The service is calling such capabilities Tactical Data in Use Security (DUCES) solutions.
“This constrained, highly dynamic, and adversarial-susceptible tactical environment will be a challenge to implement ZT solutions that meet mission needs,” the RFI reads.
The Army is turning to zero trust to protect its data as it has found that “traditional” security models aren’t making the cut anymore given the ever increasing complexity of cyber threats, according to the RFI.
The solicitation is specifically looking for solutions that offer advanced capabilities in encryption and anomaly detection in addition to “secure communication protocols” that protect against current and future threats.
The concept of zero trust has gained considerable momentum in recent years as data leaks and the proliferation of adversarial attacks on critical infrastructure have surmounted. At its core, zero trust follows the philosophy “never trust, always verify” and assumes that the network is always compromised. This means that instead of allowing users to have free reign over a network, there are constant checks to make sure that users are allowed to access what they are trying to access. This verification happens through identity, credential, and access management, or ICAM.
Related: Army picks Akamai for prototype battlefield zero trust project: T-ICAM
Monday’s RFI is not the first time the Army has searched for zero trust solutions at the tactical edge. Last spring the service chose cloud and edge-computing company Akamai to develop prototype Tactical ICAM capabilities for its combat units. However, the service didn’t go through the typical procurement process or fire out an RFI for Akamai’s prototypes. Instead it used the streamlined Software Acquisition Pathway and a flexible Other Transaction Authority contract to get Akamai’s products in the hands of the warfighters much quicker.
But this time around, the Army seems to be acquiring zero trust solutions the old-fashioned way. Responses are due before noon on March 5.