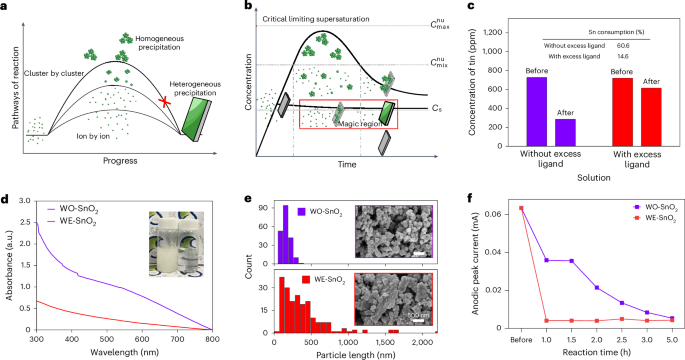
The Critical Role of Provenance in Cybersecurity and Supply Chains
The Power Inverter Kill Switch Story Underlines The Importance Of Provenance in Cybersecurity and the Supply Chain Do you really know what your production assets contain? If you’ve ever bought antiques, you’re probably familiar with the concept of provenance. I have relatives that own a dresser that was gifted from George Washington to a family […] The post The Critical Role of Provenance in Cybersecurity and Supply Chains appeared first on Logistics Viewpoints.


 The Power Inverter Kill Switch Story Underlines The Importance Of Provenance in Cybersecurity and the Supply Chain
The Power Inverter Kill Switch Story Underlines The Importance Of Provenance in Cybersecurity and the Supply Chain
Do you really know what your production assets contain?
If you’ve ever bought antiques, you’re probably familiar with the concept of provenance. I have relatives that own a dresser that was gifted from George Washington to a family friend when he was a lieutenant in the colonial army. How do we know this? Because of the authenticated documentation that came with the dresser proving its origin. This is provenance – proving and documenting where something came from, what it contains, and the path it took before it wound up in your possession.
Heavy assets in industrial automation are a lot more complex than antiques, and the stakes are a lot higher, as we saw recently with the story about cellular powered kill switches found in Chinese manufactured power inverters used in solar and wind farms. In addition to being used around the world for renewable power applications, these inverters are also used in batteries, heat pumps, EV chargers, and other assets.
It’s typical for these products to have remote access capabilities, but these connections are normally handled through firewalls. You may have read the story about Chinese manufactured cranes that have remote connectivity capabilities but are largely unsecured. Many end users were not even aware of these remote communication capabilities, or if they were, they were improperly secured. If your assets come with features and functions that present a potential cybersecurity risk to your enterprise and you don’t address it or are not aware of it even though it is documented, that’s ultimately your responsibility, not the vendor’s.
The Problem of Rogue Components
It’s not always obvious what all the components are in an asset, be they hardware or software. The more complex the asset, the more complicated the issue becomes. In the case of the power inverters, the communication devices were undocumented, and asset owners did not even know they were there. The devices were found by a US-based team of experts whose job was to strip these assets down and identify their components. According to the Reuters article referenced in the above link, the “rogue components provide additional, undocumented communication channels that could allow firewalls to be circumvented remotely, with potentially catastrophic consequences.”
What is Provenance in Cybersecurity?
In the world of cybersecurity, provenance is more than just the source of origin. According to NIST, provenance is “The chronology of the origin, development, ownership, location, and changes to a system or system component and associated data. It may also include personnel and processes used to interact with or make modifications to the system, component, or associated data.” So, it’s more than just where the product came from, it includes all the associated data about what the asset or “component” contains from both a hardware and software standpoint.

Large Power Transformers In a Storage Yard: Source: IEEE SpectrumSBOMs: What’s in Your Software?
The concept of software bills of materials (SBOM) has emerged as an important element of cybersecurity. In simple terms it contains the details and supply chain relationships of various components used in building software. Those who produce, purchase, and operate software use it to improve their understanding of what components are in the systems. This in turn has multiple benefits, most notably the potential to track known and newly emerged vulnerabilities and risks. This concept applies to all systems, including those used for manufacturing operations and control.
SBOMs are becoming increasingly mandated in new regulations across a wide range of industries. Thee White House’s 2021 Executive Order on Improving the Nation’s Cybersecurity mandated that federal agencies receive SBOMs for software they purchase. The EU’s Cyber Resilience Act (CRA) requires manufacturers of digital products sold in the EU to produce a top-level SBOM.
HBOMs: What’s in Your Hardware?
Unfortunately, SBOMs don’t do much to identify the various hardware components in an asset or system and where they come from. For that, you need an HBOM or hardware bill of materials, which should provide a detailed inventory of the hardware components included in an asset or system. CISA has its own Hardware Bill of Materials Framework for Supply Chain risk Management that you can review here and download.
HBOMs are relevant to any hardware asset, from a DCS controller or a field device like a pressure transmitter all the way up to large transformers. The larger and more complex the asset is, the more important it is to have a complete HBOM and SBOM. Take the example of large power transformers (LPTs), which again are largely sourced from China, are often custom built, and contain many hardware and software components. Many times, we don’t even know what’s in these large assets until we completely tear them down. A Chinese power transformer was sent to Sandia National Laboratory (SNL) for inspection in 2020, but even those results are classified.
End Users Need to Take Supply Chain Cybersecurity Seriously
SBOMs and HBOMs are all part of the larger issue of supply chain cybersecurity. Compiling an accurate inventory of installed systems has long been considered as one of the first steps in a cybersecurity program. Simply identifying such assets is no longer sufficient. Potential supply chain related risks can only be addressed if the provenance of all components in those assets is known. When assessing or procuring software systems or hardware it is very important to ask the supplier to list the components in the product. This may take the form of a software or hardware bill of material, but such a formal presentation may not be necessary. If the supplier is unwilling or unable to provide this information, then this should be considered when making buying choices.
Other aspects of supply chain cybersecurity include evaluating the cybersecurity posture of your software and service partners. The importance of this was shown in the SolarWinds attack. End users are increasingly reliant on their technology and service partners to keep things running, but if your partners have poor cyber resilience, it can and will directly affect your operations at some point.
The US National Institute of Standards and Technology (NIST) provides guidance for supply chain cybersecurity in the form of a special publication titled “Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations.” This document describes how to identify, assess, and respond to cybersecurity risks throughout the supply chain at all levels of an organization. It offers key practices for organizations to adopt as they develop their capability to manage cybersecurity risks within and across their supply chains.
The post The Critical Role of Provenance in Cybersecurity and Supply Chains appeared first on Logistics Viewpoints.